20 Jun 2018
Blogs
Malicious emails via WeTransfer
AUSCERT has seen direct evidence of malicious emails being sent via WeTransfer, as part of an ongoing campaign affecting Australian organisations. We have summarised our findings and provided advice, which can be found at the end of this post.
WeTransfer is a legitimate file-hosting service with a simple business model: users can upload a file, enter a recipient email address, and enter a sender email address. The uploaded file will be sent to the recipient with an explanatory email template, and the sender will also receive an email receipt.
However, WeTransfer perform minimal validation on email addresses provided by users, which is a major security hole. By default, users may enter any sender address. The WeTransfer FAQ makes it clear that they allow address spoofing on purpose:
“Our ease of use is a core value, that’s why we allow our users to enter any email address they want. This sometimes has the effect you are experiencing, where someone else uses your email address. Most likely even by mistake!”
An attacker can enter something like the following:
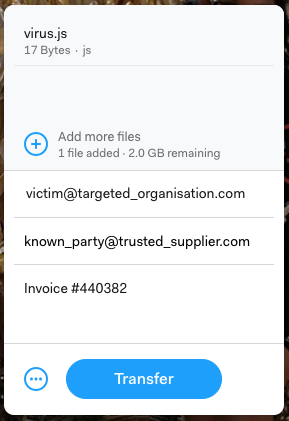
This will send a legitimate-looking file transfer email to both parties, using WeTransfer’s branding and legitimate email headers.
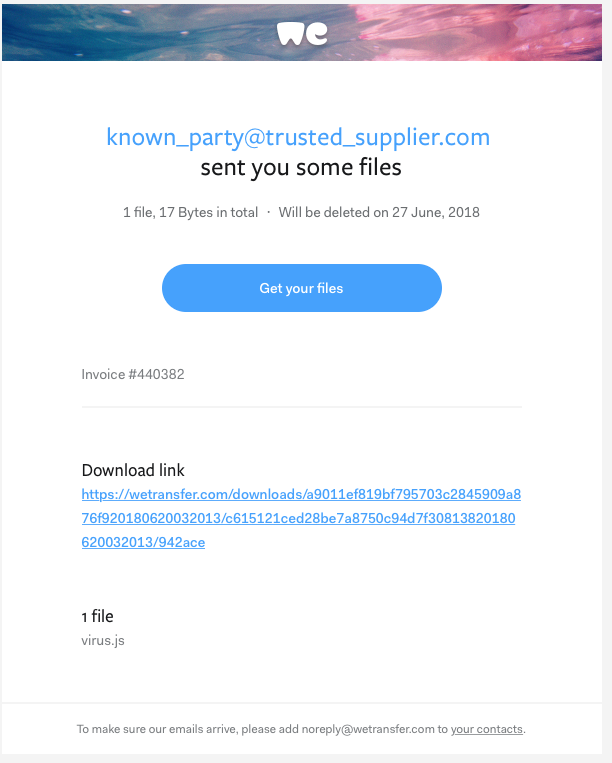
This means that WeTransfer is allowing targeted phishing and malspam emails to be delivered, based on the strength of their own brand.
This vulnerability, and others, have been known for months.
When AUSCERT contacted WeTransfer to report this security hole, we received a response, the gist of which was:
- They’ve blocked the sender and their IP address.
- They’ve removed the malicious file, so nobody can download it.
- They consider this kind of abuse a “very rare effect”.
- They have a “new email verification feature”. Fill out a form and they’ll send a verification token to your email address every time it is used as a sender.
- They can block a specific email address so it cannot be used to send spam.
This is inadequate, for the following reasons:
- Verification of the sender should be default, not opt-in.
- IP address blacklists provide minimal security.
- It is not the responsibility of an organisation or individual to disallow third-party services from spoofing them.
AUSCERT recommends:
- All emails sent from WeTransfer should be treated as suspicious.
- Until mail blacklists begin to block WeTransfer’s emails automatically, flag suspicious emails as junk.
- Mail administrators should consider looking for recent WeTransfer emails and following up with users. Malicious emails are sent from noreply@wetransfer.com.




