5 Jul 2022
Blogs
As one financial year ends and another begins, Australians start preparing their tax applications and with it, an increase in the frequency and scope of tax-related phishing is expected.
We are going to look at various methods a scammer/attacker might use to obtain your personal information such as username, password, credit card details, contact details or any other information that identifies you as you. This personal information is then used fraudulently or to conduct further malicious activities depending on the data obtained.
Email phishing
Email phishing is one of the most common methods used to obtain your personal information. The sender imitates the Australian Tax Office (ATO) or MyGov and sends a phishing email that looks like a legitimate email. The spoofed email address may be difficult to detect when the recipient is using a phone as typically, it does not show the actual email address in full, revealing who it was sent from.
- a. Email with a Phishing URL
Usually, such emails contain a phishing link that when clicked, redirects the user to a website asking for personal information. Emails that request the recipient to enter their details, such as bank account information, could lead to fraud.
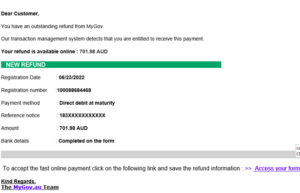
Example of malicious email with a phishing URL
- b. Email with a local HTML attachment
Some emails will not contain any phishing URLs within the body of the email. Instead, the email will have an HTML file as an attachment. When a user opens the HTML attachment, it will link to a phishing form requesting the user enter a username and password. The HTML file contains code that sends the credentials to the attacker (if entered). Such techniques are used to avoid email security software.
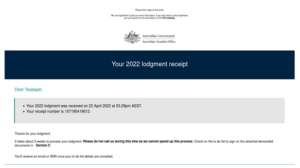
Example of malicious email with an HTML attachment
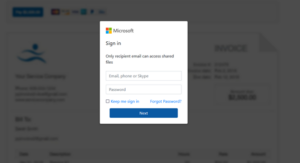
Example of malicious email with an HTML phishing form
Smishing (SMS Phishing)
As consumers become more aware of potential threats and scams, attackers develop new methods to target and trick recipients. One such method is smishing.
This method is quite simple as the fake texts are disguised to come from a known and trusted source such as a bank or, the ATO.
In this instance, a text message with a URL is sent to a phone number pretending to be MyGov. When clicked, the user is redirected to a MyGov phishing page where they are required to enter personal information. Additionally, it could then redirect the user to a secondary phishing page made to look like a bank.
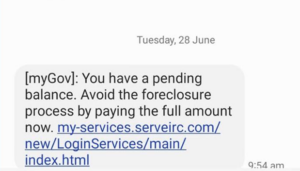
Example of malicious phishing link in SMS/Text Message (1)
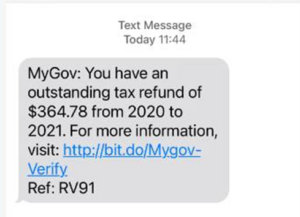
Example of malicious phishing link in SMS/Text Message (2)
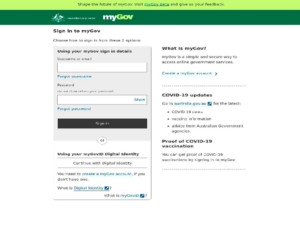
Example of phishing page (MyGov)

Example of phishing page redirecting to secondary phishing page (MyGov to a bank)
It is important to know that ATO or MyGov would not send any email or text message directly to ask for any personal information. Should you receive a suspicious email or SMS, please report it to ReportEmailFraud@ato.gov.au or contact ATO.
If something looks suspicious, be it the spelling, website address or the request within the message, do not click the link or proceed!
ATO is a member of AUSCERT and we help ATO in deactivating such phishing websites. AUSCERT members have access to the Malicious URL Feed which is automatically populated with malware and phishing links as AUSCERT’s Analyst Team processes them and is updated every 15 minutes.
Additional indicators (over and above the malicious URLs) such as email content, and phish page screen captures, can be found in AUSCERT’s Member Security Incident Notifications (MISP).
Further information on the mentioned services can be found at the links below:




