26 Jul 2024
Member information
AUSCERT Bulletin Formats
AUSCERT publishes two security bulletin formats:
- External Security Bulletin (ESB) – produced by vendors that are summarised and re-released by AUSCERT in a consistent format.
- AUSCERT Security Bulletin (ASB) – produced by AUSCERT with Overview, Impact and Mitigation information. ASBs typically describe critical vulnerabilities and emerging threats. They are collated from a variety of resources including vendors, security researchers and incident response teams around the world.
Every AUSCERT bulletin contains a Bulletin Summary which highlights the essential information to assist in the vulnerability management process. The Bulletin Summary consists of the following categories (where relevant):
- Product
- Publisher
- Operating System
- Resolution
- CVE Names
- Original Bulletin URL
- Comment
- CVSS (Max)
- EPSS (Max)
- CISA KEV (if applicable)
These categories are described in further detail below.
ESB Structure
Bulletin Titles and Email Subject Lines
Bulletin titles and bulletin email subject lines display information in a concise format.
The title includes the bulletin ID (eg ESB-2024.1234), revision number if applicable (eg ESB-2024.1234.2) and may include an ‘ALERT’ flag if the contents of the bulletin are time critical or reference a serious actively exploited vulnerability.
The title also lists operating systems or hardware types that the vulnerability affects, and the product or product family.
Example of a bulletin title: ESB-2024.1234 libarchive
Example of an email subject line: ESB-2024.1234 [SUSE] libarchive: CVSS (Max): 7.3
Bulletin Header
The bulletin header consists of the ESB (or ASB) ID, a short summary of the purpose of the bulletin, and the date.
Bulletin Summary
The bulletin summary is an overview of the essential information in the bulletin typically used in the vulnerability management process. Both ESBs and ASBs contain a summary with individual fields as shown in this example:
Product
The product field displays the affected product name and version numbers (if any). Both ESBs and ASBs will have a Product field.
Publisher
Only present in an ESB, the Publisher field gives the name of the original source of the bulletin. This is often a vendor such as SUSE or Red Hat but it may also be another security team or research group.
Operating System
This field gives a list of operating systems or operating system families that are affected by the vulnerability.
Resolution
The Resolution field gives a quick indication on how to protect against the vulnerability. The values are:
None: No resolution is currently available.
Patch/Upgrade: A patch or new, unaffected version of the product is available. Note that only official vendor patches are acceptable as a patch – third party patches would be considered a mitigation.
Mitigation: There are mitigation steps available that may be used, however there is no specific fix to the vulnerability.
Alternate Program: Another program with similar functionality is available that is not vulnerable.
CVE Names
This field lists any CVE identifiers that relate to this vulnerability. CVEs are effective for tracking vulnerabilities that affect multiple products.
Original Bulletin URL
This field lists the URL of the original bulletin source. The original bulletin will often have additional links for further information.
Comment
This field contains any additional information that AUSCERT believes should be highlighted, including:
- CVSS (Max)
- EPSS (Max)
- CISA KEV (if applicable)
These categories are described in detail further below.
CVSS (Max)
The Common Vulnerability Scoring System, or CVSS score, is included in all AUSCERT ASBs and ESBs in the Comment field. The CVSS is a published standard for assessing security vulnerabilities which classifies and scores vulnerabilities based on their severity. Scores are calculated based on a formula that depends on several metrics including required access, impact and authentication. The scores range from 0 to 10, with 10 being the most severe.
This field consists of the CVSS (Max) CVSS Score, CVE-ID and CVSS description of the CVE with the highest score. If there is no CVSS (Max) score available at the time of publishing, the Comment field will show as “CVSS (Max): None”.
For further information about how the CVSS (Max) is calculated and used, please see https://auscert.org.au/blogs/bulletin-impact-access-to-cvss-migration.
EPSS (Max)
Where an Exploitation Prediction Scoring System (EPSS Score) is available, this will also be included in the Comment field of a bulletin as “EPSS (Max)”. EPSS employs advanced algorithms to forecast the likelihood of vulnerabilities being exploited in real-world scenarios. A higher EPSS score will indicate a higher risk of exploitation which may provide input into the vulnerability management process.
The syntax of the EPSS (Max) score is:
EPSS (Max): (*Probability) (**Percentile) (CVE Number) (Date EPSS calculated).
Probability: The likelihood of exploitation of the given CVE within the next 30 days
Percentile: The vulnerability’s relative severity compared to others, ranking it within a distribution of similar security issues based on their assessed risks and potential impacts.
AUSCERT advises members to research EPSS thoroughly before considering its application in vulnerability management. Understanding EPSS can require effort, and its suitability can vary depending on the environment.
See articles below for further details on use and interpretation:
- https://www.first.org/epss
- https://www.first.org/epss/user-guide
- https://www.first.org/epss/faq
- https://vulners.com/blog/epss-exploit-prediction-scoring-system/
- https://blog.stackaware.com/p/deep-dive-into-the-epss
- https://asimily.com/blog/epss-and-its-role-in-vulnerability-management/
- https://security.cms.gov/posts/assessing-vulnerability-risks-exploit-prediction-scoring-system-epss
CISA KEV
A CISA Known Exploited Vulnerability (KEV) is also present in the Comment field if applicable. The KEV catalogue is a CISA-maintained authoritative source of vulnerabilities that have been exploited in the wild. It is recommended that all members review and monitor the KEV catalogue and prioritize remediation efforts of the listed vulnerabilities to reduce the likelihood of compromise by known threat actors.
The field consists of the CISA KEV CVE(s) and the CISA KEV url for reference.
For example:
For further information about CISA KEV, please see https://www.cisa.gov/known-exploited-vulnerabilities.
Bulletin Updates and Versioning
An ESB or ASB can be updated in the event of crucially new or updated information becoming available since the original date of publication.
Updates will have a version number appended to the bulletin ID, eg ESB-2024.1234 will become ESB-2024.1234.2, and the ‘UPDATE’ tag will be added.
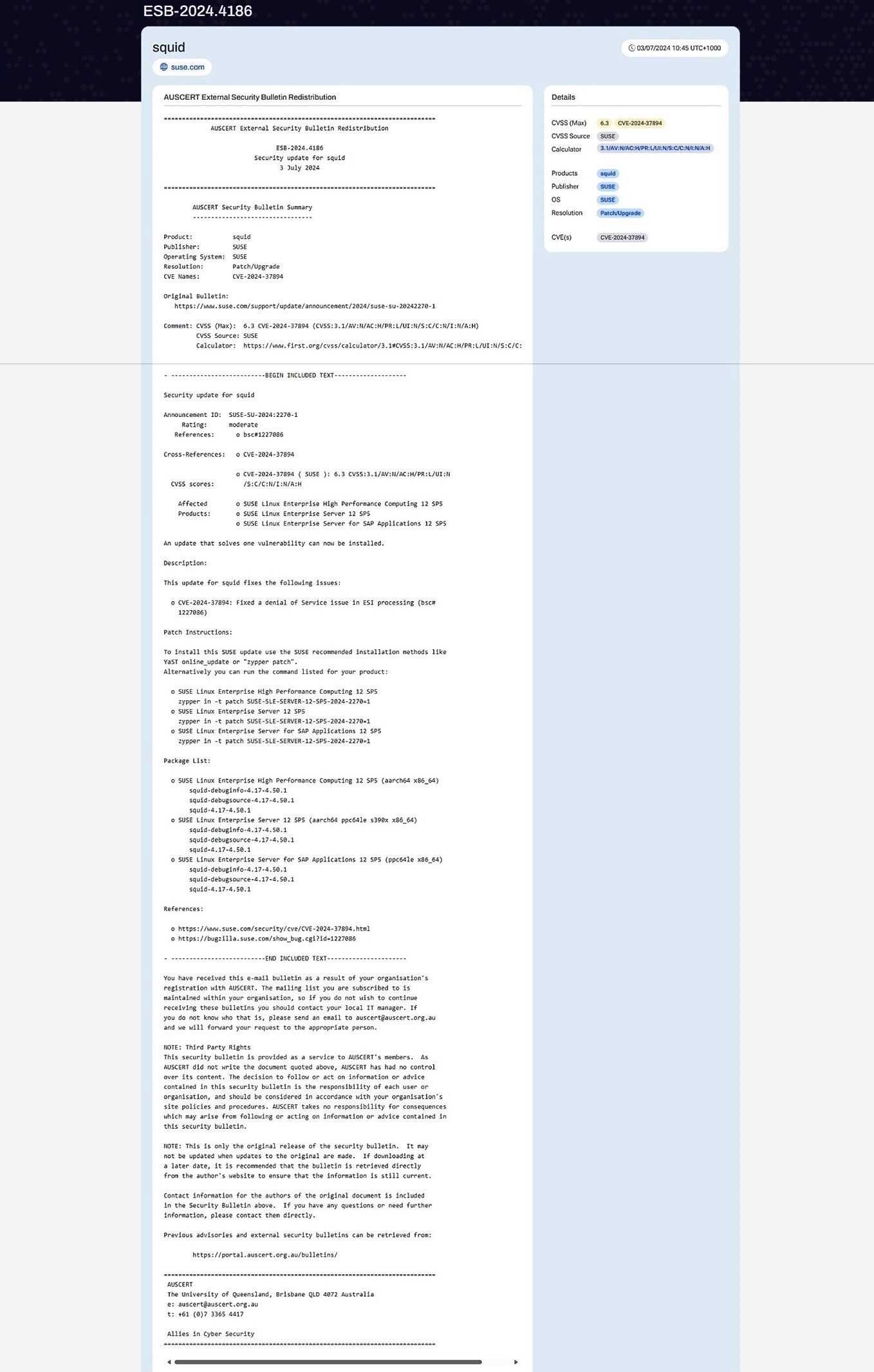
ASB Structure
An ASB contains the same bulletin title, bulletin header, bulletin summary and comment sections as an ESB, however the main body of an ASB differs from an ESB.
The main body of an ASB generally consists of four headings:
OVERVIEW: This is a summary of the vulnerability being reported and the products that are affected.
IMPACT: This section outlines in more detail what the vulnerability allows attackers to perform (eg remote code execution), and the potential outcome of these vulnerabilities (eg significant data breaches, circumvent firewalls, intrusion detection systems, etc).
MITIGATION: This section outlines steps to mitigate the risk. This can range from applying available patches to address the vulnerability to restricting or segmenting access to the network, including deploying additional monitoring and alerts against specific criteria.
REFERENCES: This is a list of websites that report on the vulnerability. It can be a third-party website or the vendor itself. The websites are referenced within the ASB as the source of information being reported.
Examples
Full example of an ESB:
Full example of an ASB: