2 Feb 2025
Member information
A guide to AUSCERT Member Security Incident Notifications: MSINs
Introduction
The Member Security Incident Notifications (MSINs) service provides crucial alerts and insights on security incidents affecting members.
What is an MSIN?
An MSIN is a daily customised composite security report targeted towards AUSCERT member organizations. It contains a compilation of “security incident reports” as observed by AUSCERT through its threat intelligence platforms.
MSIN Dashboard
As part of this service, a dashboard view provides high level statistics along with the ability to search and filter organisational alerts. The dashboard is accessible at https://portal.auscert.org.au/msins
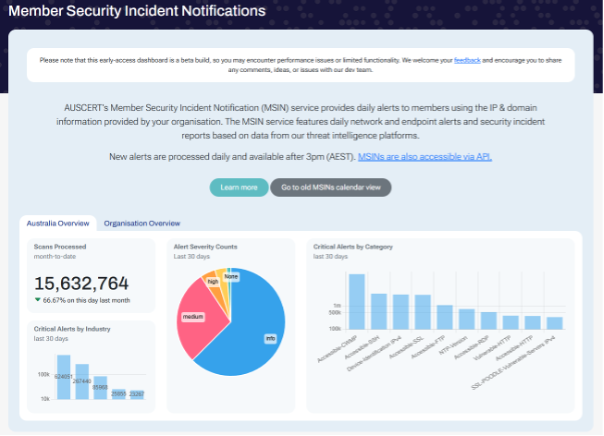
MSIN Dashboard Statistics Tabs
The Australia and organisation statistics tabs provide insights into both nation-wide and your own organisation’s MSIN alerts. Near the beginning of the week, it is not unusual for your organisation’s statistics to show zero or be blank, as alerts are ingested into AUSCERT’s systems around 3pm each day, and it can take up to 24-48hours for the charts to be updated.
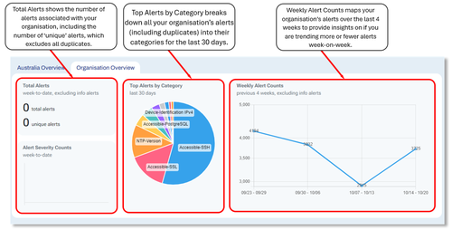
MSIN Results Table
The results table is the primary interface for your organisation’s MSIN alerts and allows you to perform advanced searches, sort and filter your alerts, view the full details as well as exploring the CVEs associated with them by clicking through to the external NVD links for each CVE.
By default, this view will show all alerts excluding “info” level alerts in the last 48 hours for your organisation. 48 hours has been chosen as it factors in the ~24 hour delay that occurs while MSIN alerts are ingested and processed by AUSCERT’s systems.
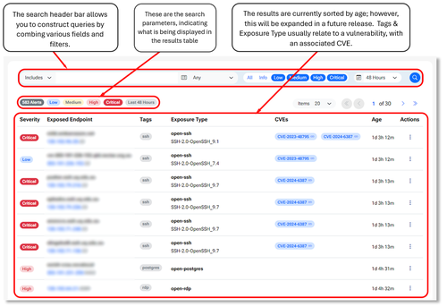
MSIN Details Page
Under the actions column for every MSIN, the three dots dropdown can be expanded to open up the details popup for each alert. This shows all available information relating to the MSIN and may contain extra information relating to specific alerts. Source reference links for additional context can also be viewed here.
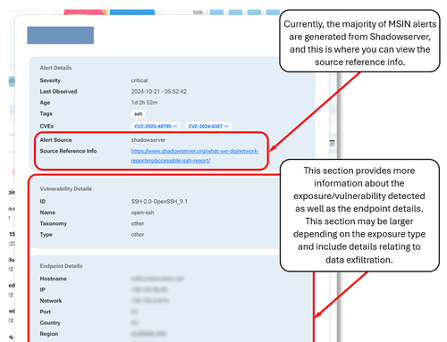
Further Information
Daily
- MSINs are processed and issued daily
- MSINs are only issued if at least one incident report specific to the member is detected within the past 24-hour period
- If there are no incidents to report, no MSIN will be issued. The more security incidents spotted corresponding to your organization, the more incident reports will be included in the MSIN and the larger the MSIN is received
Customised
- MSINs are tailored for each member organization, based on IPs and Domains provided
- To receive accurate and useful MSINs, it’s important this information updated is kept updated in your membership profile (see FAQ below)
Severity
Individual events in MSINs are categorised into the following severity levels:
- Critical
Highly critical vulnerabilities that are being actively exploited, where failure to remediate poses a very high likelihood of compromise. For example, a pre-auth RCE or modification or leakage of sensitive data
- High
End of life systems, systems that you can log into with authentication that are meant to be internal (SMB, RDP), some data can be leaked. Sinkhole events end up in this category.
- Medium
Risk that does not pose an immediate threat to the system but can over time escalate to a higher severity. For example, risk of participating in DDoS, unencrypted services requiring login, vulnerabilities requiring visibility into network traffic (MITM without being able to manipulate the traffic) to exploit, attacker will need to know internal systems/infrastructure in order to exploit it.
- Low
Deviation from best practice – little to no practical way to exploit, but setup is not ideal. Vulnerabilities requiring MITM (including manipulating the traffic) to exploit. For example, SSL POODLE reports may end up in this category.
- Info
Informational only. Review in accordance with your security policy.
These severity levels are based on those used by Shadowserver. Events which have not been assigned a severity will be marked as Unknown.
A summary of reports by severity level can be found at the top of your MSIN. For example:
Summary of reports based on severity: * Critical: accessible-ssh 3 * High : vulnerable-exchange-server 1 * Medium : accessible-cwmp 1
The MSIN subject will be prefixed with the highest-level severity seen in the report. For example:
[Severity:CRITICAL] AusCERT Member Security Incident Notification (MSIN) for “Member Name”
Composite
- Each MSIN could potentially consist of multiple incident TYPE reports. For example, it could contain an Infected Hosts report which highlights hosts belonging to a member organization that have been spotted attempting to connect to a known botnet C&C server, followed by a DNS Open Resolvers report listing open recursive DNS resolvers that could be used in a DNS amplification DDoS attack.
- Each incident type report could also include multiple incident reports. For example, this “infected hosts” report contains 2 incidents:
Incidents Reported
Timestamp: 2015-08-25T00:20:34+00:00
Drone IP: 123.456.789.abc
Drone Port: 13164
Drone Hostname: abc.xxx.xxx.xxx.au
Command and Control IP: aaa.bbb.ccc.ddd
Command and Control Hostname: imacnc1.org
Command and Control Port: 80
Malware Type: redyms
Timestamp: 2015-08-25T00:20:34+00:00
Drone IP: 321.654.987.cba
Drone Port: 2343
Drone Hostname: def.xxx.xxx.xxx.au
Command and Control IP: ddd.eee.fff.ggg
Command and Control Hostname: imacnc2.org
Command and Control Port: 123
Malware Type: dyre
All timestamps are in UTC.
It is imperative that these incidents be reviewed and handled individually.
Structure
An MSIN has the following basic structure.
==================HEADING FOR INCIDENT TYPE 1================== Incident Type Name of the incident and any known exploited vulnerabilities and associated CVEs. Incident Description Further information on potential attack vectors and impacts. Incidents Reported List of individual reports sighted by AUSCERT Incident report 1 Incident report 2 … Incident report n AUSCERT recommended mitigations Steps for resolution of incidents or mitigation of vulnerabilities which could be exploited in the future.
References Links to resources referenced within the report.
Additional Resources Links to additional material such as tutorials, guides and whitepapers relevant to the report aimed at enhancing the recipients understanding of the addressed vulnerabilities, potential impacts and mitigation techniques. =============================END OF REPORT========================= =====================HEADING FOR INCIDENT TYPE 2=================== Incident Type Incident Description Incidents Reported Incident report 1 Incident report 2 … Incident report n AUSCERT recommended mitigations References Additional Resources =============================END OF REPORT========================= … … =====================HEADING FOR INCIDENT TYPE X=================== =============================END OF REPORT=========================
MSINs API Overview
The MSINs API provides two endpoints for querying and retrieving information about MSINs.
Base URL
https://portal.auscert.org.au/api/msins/v1/
Authentication
All endpoints require API key authentication. Include your API key in the request headers as follows:
1 | API-Key: <your_api_key>
Endpoints
Search MSINs
Returns a list of MSINs matching the specified parameters or default values.
- Endpoint: /search
- Method: GET
Get MSIN Details
Returns the detailed information for a single specified MSIN object.
- Endpoint: /get
- Method: GET
Frequently Asked Questions
1. How can I update domain/IP information for my organisation?
If you are a Primary AUSCERT contact simply email AUSCERT Membership at membership@auscert.org.au and provide the updated information. If you have a privileged account in the Member portal you can request changes through the portal.
AUSCERT will perform a validation check to ensure the domains are under your organisation’s ownership or control prior to including them in the monitoring list.
2. Where does the information in an MSIN come from?
AUSCERT receives information relating to compromised and/or vulnerable resources from several trusted third parties, through secure means.
The trust relationship between AUSCERT and third parties entails conditions which prevent disclosure of the source(s) of information.

